Are you concerned about ensuring project security while outsourcing project work? You often share confidential information when partnering with a third party or vendor for a project. Suppose your organization works with several vendors and has many ongoing projects. In this case, it is more complicated for all stakeholders to determine which vendors work on which project, mainly if the stakeholders are not directly involved. This lack of oversight can result in project security risks and leaks.
Start is a vendor risk management platform featuring a project module that improves project security and risk mitigation. It allows organizations to track vendors and their access under a Project Profile across different levels.
The Importance of Project Security With Project Profiles
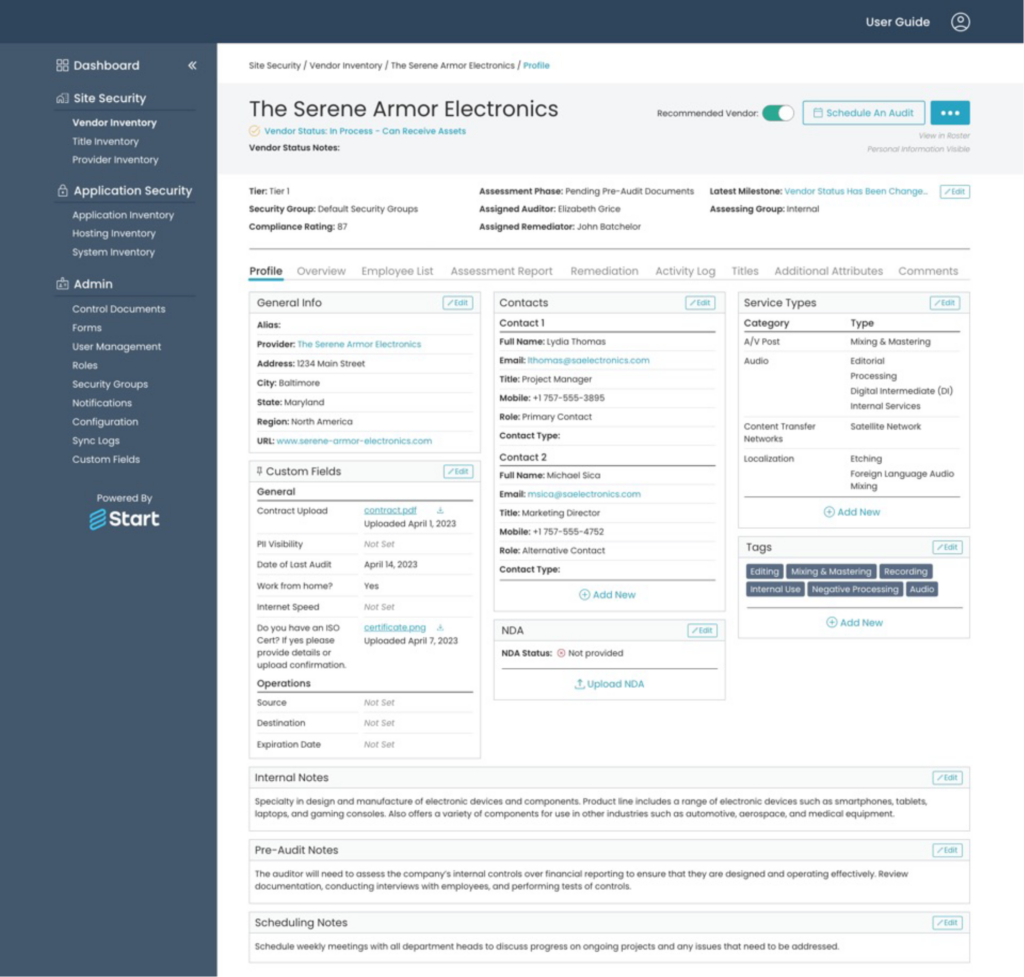
For organizations with several ongoing projects in production, internal stakeholders must be aware of the third parties with access to each project. With Project Profiles, you can see how vendors directly impact your company’s project security and intellectual property (IP).
Project Profiles include vendor information, such as:
- What assets of the project is the vendor working on
- What is the vendor’s current security assessment status
- What services the supplier is providing, e.g. prototype destruction
- What software is in use for each project
Having complete visibility on all of these items helps to mitigate risks and provides a starting place to look in case a project is ever compromised.
Using Project Profiles in Start
Under a Project Profile in Start, internal users can link vendors and the applications they use for projects. Project Profiles provide complete visibility on each vendor’s services, what assets they handle, and which business users have created the links. Tracking which applications are used for the project makes organizations aware of potential software vulnerabilities and how they will affect your IP.
Use Cases From Our Clients
Our clients in Media and Entertainment use Project Profiles to track film and media titles. If someone leaks dailies, the studio can review who handled the dailies for that title, narrowing down the source and cause of the leak.
In Electronics Manufacturing, our clients use Project Profiles to track new physical hardware and close the supply chain loop. Project Profiles provide centralized visibility on who has access to physical hardware and essential information, like who is responsible for destroying them to prevent IP theft.
Start is Fully Customizable
All organizations manage projects differently; what works for organizations in Electronics Manufacturing may not work for those in Media and Entertainment. It is up to each organization to determine what information they want to track on a project. Start supports custom fields, so organizations can add any attributes to a Project Profile that they consider valuable. For example, you can include items from the vendor questionnaire on a profile.
Internal Security Measures
In Start, Project Profiles are accessible from the Start Admin and Start Roster portals. If projects are susceptible and want to limit internal access, organizations can hide them from the project inventory in the Start Roster. This extra layer of project security ensures that only administrative users can access the project and further limits risks around accidental leaks or IP theft.
Ensure Project Security With StartVRM
When it comes to managing partnerships with third parties and vendors, ensuring apparent oversight is essential for the security and success of your projects. Start uses Project Profiles to enhance risk mitigation and project visibility. By enabling organizations to track vendors and their access at a project-specific level rather than just at the vendor level, you can proactively safeguard your projects and maintain their integrity. To learn more, chat with our vendor risk management experts.